
- Introduction to Azure Sentinel
- Key Features and Capabilities of Azure Sentinel
- How Azure Sentinel Works in Security Operations
- Setting Up and Configuring Azure Sentinel
- Data Collection and Integration with Other Microsoft Security Services
- Detecting Threats with AI and Machine Learning in Azure Sentinel
- Best Practices for Implementing Azure Sentinel
- Conclusion
Introduction to Azure Sentinel
Azure Sentinel is a cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) solution that delivers intelligent security analytics and advanced threat protection across an organization’s entire IT ecosystem. Built on Microsoft Azure, it provides real-time threat detection, proactive hunting, and automated response capabilities to safeguard businesses against evolving cyber threats. By leveraging artificial intelligence (AI) and machine learning (ML), Azure Sentinel correlates security events from multiple sources, including cloud, on-premises, and hybrid environments. It integrates seamlessly with Microsoft security solutions (such as Microsoft Defender and Azure Security Center), supports Microsoft Azure Training , and connects with a wide range of third-party tools, offering a centralized platform for security operations teams. Azure Sentinel empowers organizations with scalability, automation, and intelligent insights, reducing the complexity and cost of managing traditional SIEM systems. With features like advanced threat hunting, automated playbooks, and AI-driven analytics, businesses can detect, investigate, and respond to cyber threats faster and more efficiently, ensuring a robust security posture in today’s dynamic threat landscape.
Key Features and Capabilities of Azure Sentinel
- Cloud-Native Architecture : As a fully cloud-based SIEM platform, Azure Sentinel requires minimal on-premises infrastructure, ensuring scalability, flexibility, and ease of management. Organizations can quickly scale Sentinel up or down according to their needs without worrying about hardware capacity or maintenance.
- Integration with Multiple Data Sources: Azure Sentinel integrates with a wide range of data sources from within Microsoft’s ecosystem and third-party services. It can pull data from security solutions, firewalls, networking appliances, servers, and IoT devices to provide a unified view of security events.
- Advanced Threat Detection : Azure Sentinel leverages built-in Career in AI and Machine Learning to detect real-time advanced threats and anomalies. It uses behavioral analytics to correlate vast amounts of data and identify patterns that may indicate potential security breaches, attacks, or vulnerabilities.
- Incident Management and Response: Sentinel provides tools for investigating security incidents, automating responses, and streamlining incident management. It helps security teams prioritize and coordinate responses to threats through a centralized platform, ensuring a faster and more efficient response time.
- Automation and Orchestration : With Azure Sentinel’s playbooks and automation capabilities, security operations teams can automate repetitive tasks, enabling faster incident resolution. For instance, you can automate threat containment, block IP addresses, or trigger notifications to appropriate stakeholders.
- Built-in and Customizable Analytics : Azure Sentinel includes pre-built analytics rules for common security scenarios, such as brute-force attacks or data exfiltration attempts. Additionally, users can create custom analytics rules to meet their specific security requirements, ensuring tailored detection and monitoring.
- Security Insights and Visualization : Sentinel provides rich visualizations through dashboards and workbooks, allowing security analysts to interpret complex security data easily. These dashboards offer real-time insights into security incidents, enabling security teams to monitor the health of their environment and make informed decisions.
- Centralized Log Management : Azure Sentinel aggregates security data from various sources and stores it in Azure Log Analytics. This centralized logging service enables organizations to store, query, and analyze security-related logs, making detecting trends, patterns, and historical security incidents more manageable.
- Create an Azure Sentinel Workspace To get started, you must create a Log Analytics workspace in Azure. This workspace acts as the central repository for your data and configurations. Azure Sentinel is built on the Log Analytics platform, so creating a workspace is the first step to integrating Sentinel with your security environment. Additionally, incorporating Data Analytics With Azure Stream enables real-time data processing and enhances your ability to detect and respond to threats quickly, making your security operations more proactive and efficient.
- Connect Data Sources After setting up your workspace, the next step is to connect your data sources. Azure Sentinel can pull data from various Microsoft services (e.g., Microsoft Defender, Office 365) and third-party products (e.g., firewalls, antivirus software, or intrusion detection systems). Connecting these sources is critical to ensuring that Sentinel can analyze and correlate data across your environment.
- Configure Analytics Rules Once your data sources are connected, you must configure analytics rules to detect suspicious behavior. Azure Sentinel provides built-in detection rules, but you can customize them to fit your organization’s needs. The rules will use machine learning and behavioral analytics to identify real-time anomalies.
- Set Up Incident Response Playbooks After configuring the analytics rules, you can set up playbooks for incident response. These playbooks are automated workflows that can take predefined actions when specific conditions are met. For example, if an endpoint is compromised, a playbook could automatically isolate the device from the network to prevent further damage.
- Monitor and Visualize Data Use Azure Sentinel’s dashboards and workbooks to monitor real-time security data. These dashboards provide valuable insights into potential threats, helping analysts identify patterns, anomalies, and ongoing incidents across the organization’s network.
- Microsoft Defender for Identity
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Azure Active Directory (AAD)
- Anomaly Detection As covered in the Microsoft Azure Course , Sentinel uses machine learning models to detect deviations from normal behavior. This could include unusual login patterns, abnormal file access, or unexpected traffic spikes. By continuously learning from historical data, Sentinel can identify new and emerging threats that conventional methods may miss.
- Behavioral Analytics Sentinel applies behavioral analytics to understand how users and devices interact with the environment. Analyzing patterns of behavior can detect when an entity behaves differently, such as by accessing data it doesn’t normally interact with or engaging in suspicious activity.
- Centralized Logging: Collect logs from all critical systems and applications to ensure comprehensive security monitoring.
- Fine-tune Detection Rules: Customize detection rules to reduce false positives and ensure high-fidelity alerts.
- Integrate with Existing Tools: Leverage Sentinel’s integration with Microsoft security tools and third-party services to create a unified security ecosystem aligned with Cybersecurity Framework such as NIST, enabling comprehensive threat detection, response, and compliance.
- Regularly Test and Update Playbooks: Ensure that incident response playbooks are periodically tested and updated to handle evolving threats.
Azure Sentinel offers a comprehensive set of features that make it a powerful tool for managing security operations across diverse environments:
Eager to Acquire Your Microsoft Azure Certification? View The Microsoft Azure Training Offered By ACTE Right Now!
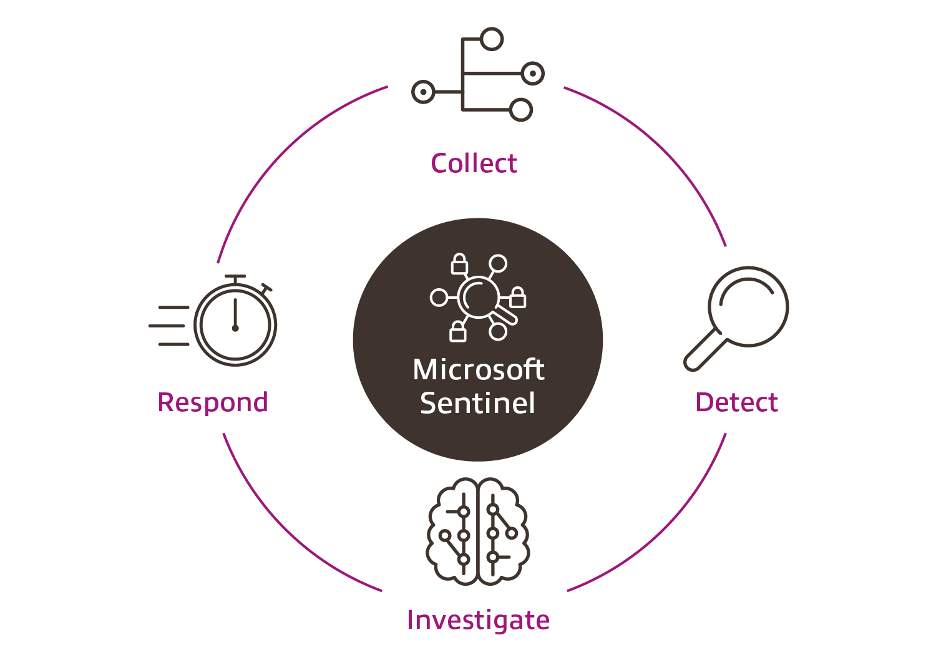
How Azure Sentinel Works in Security Operations
Azure Sentinel helps organizations streamline their security operations by providing a centralized platform for data collection, threat detection, incident response, and automation. Here’s how it functions. Azure Sentinel collects security data from various sources, including security solutions, cloud services, and on-premises systems. This data is stored in Azure Log Analytics, which can be queried, analyzed, and visualized. Sentinel integrates with many Microsoft security services, such as Microsoft Defender for Identity, Microsoft Defender for Endpoint, Microsoft Defender for Office 365, and Azure Policy , allowing users to correlate security data across multiple platforms. Using built-in AI and machine learning models, Azure Sentinel continuously analyzes security data to identify potential threats and anomalies. It correlates events across different sources to detect sophisticated attacks that might go unnoticed. Based on these detections, Sentinel automatically generates alerts for suspicious activities. When Azure Sentinel detects a potential security incident, it creates an alert and classifies the threat based on its severity.
Excited to Obtaining Your Microsoft Azure Certificate? View The Microsoft Azure Online Training Offered By ACTE Right Now!
Security analysts can investigate these incidents further, using Sentinel’s powerful query tools to drill into the data and gather more context. If the incident requires action, the analyst can trigger automated responses using playbooks, such as blocking an IP address or isolating an infected machine. Azure Sentinel provides built-in playbooks that can automate common security response tasks. For example, a playbook can automatically notify the security team by email when a high-severity alert is triggered. These playbooks can also integrate with other security systems to isolate compromised resources or mitigate the impact of an attack. Sentinel integrates with third-party security tools, creating a unified security operations center (SOC) where analysts can orchestrate responses across multiple platforms. This reduces the need for manual intervention and ensures swift and efficient responses to security incidents.
Setting Up and Configuring Azure Sentinel
Cloud Computing Master’s Degree in Cloud Computing? Enroll For Cloud Computing Master Certification Today!
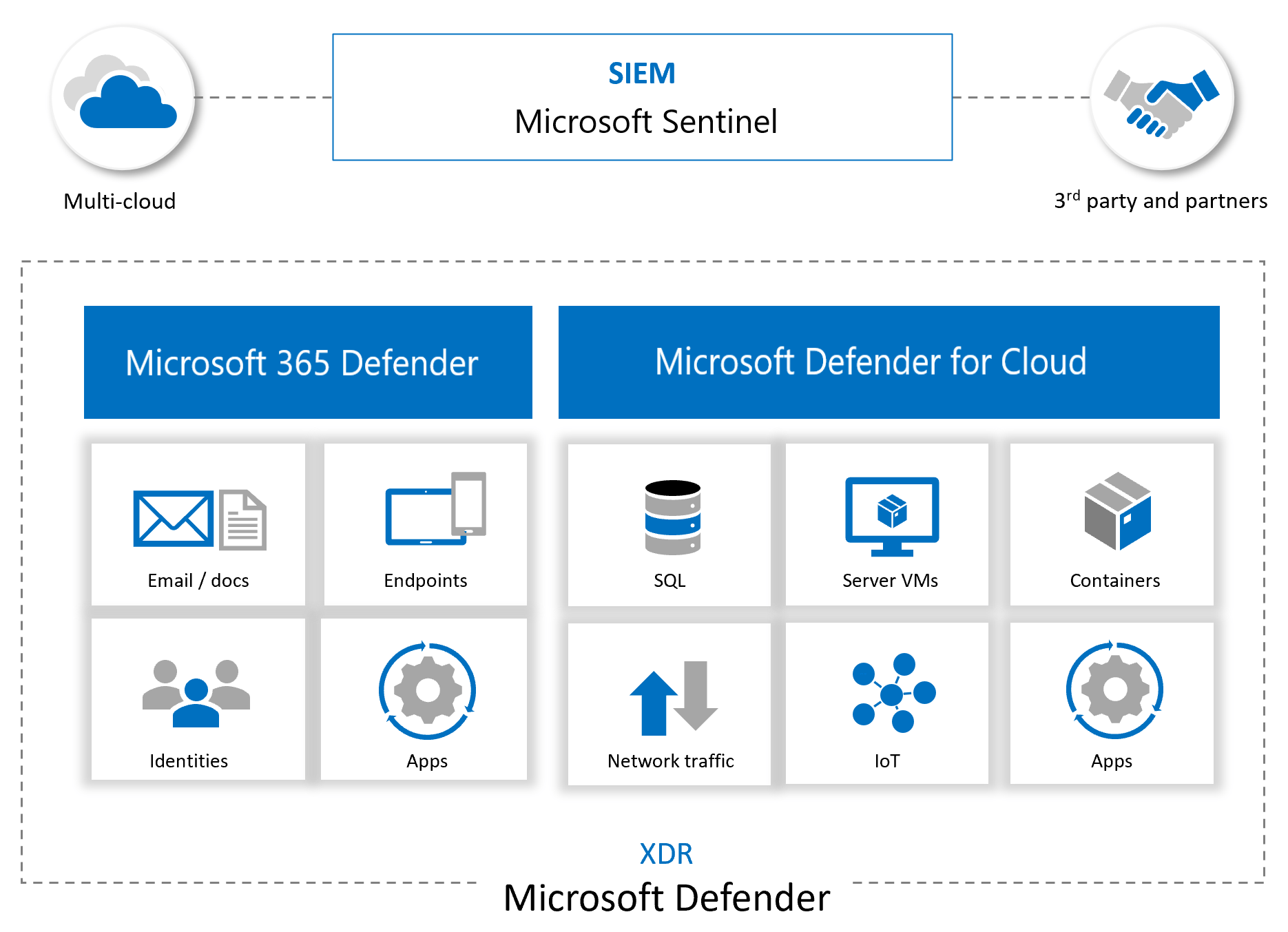
Data Collection and Integration with Other Microsoft Security Services
Azure Sentinel integrates seamlessly with several Microsoft security products, offering enhanced visibility and a more comprehensive security posture. Some key integrations include:
This service provides identity protection and threat detection capabilities, helping organizations detect and respond to identity-related threats such as password spraying or privilege escalation attempts. Sentinel integrates with Microsoft Defender for Identity to collect relevant data and trigger alerts. Defender for Endpoint is designed to protect devices from advanced threats, such as ransomware, zero-day exploits, and other malware. Sentinel integrates with Defender for Endpoint to analyze device data and detect suspicious behavior or attacks. This service, covered in Microsoft Azure Training , offers protection against email-based threats like phishing and malware. Sentinel integrates with Defender for Office 365 to pull in email and user activity data, helping security teams identify attacks that target enterprise communication channels. Azure Sentinel can collect data from the Azure Active Directory, which manages user identities and access to cloud resources. By integrating with AAD, Sentinel can detect abnormal authentication attempts, suspicious sign-ins, and other potential threats related to identity and access management key concepts often covered in course.
Set to Ace Your Microsoft Azure Job Interview? Check Out Our Blog on Microsoft Azure Interview Questions & Answer
Detecting Threats with AI and Machine Learning in Azure Sentinel
One of the standout features of Azure Sentinel is its use of artificial intelligence and machine learning for threat detection. Sentinel’s AI models analyze vast amounts of security data to identify potential threats that may go unnoticed by traditional rule-based detection methods. Here’s how it works:
Best Practices for Implementing Azure Sentinel
By following these best practices, organizations can fully leverage Azure Sentinel’s capabilities to enhance their security operations and respond more effectively to emerging threats.
Conclusion
Azure Sentinel is a powerful, cloud-native SIEM and SOAR solution that empowers organizations with intelligent security analytics and automated threat detection. By leveraging AI, machine learning, and seamless integrations with Microsoft and third-party security tools, Azure Sentinel provides a centralized platform for monitoring, detecting, investigating, and responding to security threats in real time. With its scalable architecture, automation capabilities, and advanced analytics, Azure Sentinel enables businesses to strengthen their security posture while optimizing costs and operational efficiency. By implementing best practices—such as fine-tuning detection rules, integrating with existing security tools, participating in Microsoft Azure Training , and regularly updating incident response playbooks—organizations can maximize the value of Azure Sentinel and proactively defend against evolving cyber threats. As cyber threats become more sophisticated, having a robust security operations platform like Azure Sentinel is crucial for modern enterprises. By adopting and effectively managing Azure Sentinel, businesses can enhance their security resilience, streamline incident response, and maintain a proactive approach to cybersecurity.





